Microsoft Exchange Server Zero-Day Vulnerability Exploited
Chinese hackers have infiltrated hundreds of thousands of on-premise Microsoft Exchange Server instances worldwide. Microsoft, which identified the primary attacker as Hafnium, is urging organizations running the email server to install newly released security patches. Hafnium is a nation-state actor. The group has penetrated more than 30,000 organizations in the United States alone.
While most attacks have been against servers located in the United States, threat actors have been targeting the servers of governments, law firms, and private companies in other parts of the world.
There were three stages to the attacks. First, hackers would gain access to an Exchange Server, either with stolen passwords or by using the previously undiscovered vulnerabilities to disguise themselves as someone with access. Second, they would create a web-shell to control the compromised server remotely. Third, they would use that remote access to steal data from an organization’s network.
The impact of the Microsoft Exchange Server vulnerability could be massive, possibly thousands of servers compromised per hour globally. If the predicted number of victims is this high, the potential impact would be higher than the 18,0000 organizations compromised by December’s SolarWinds. Hafnium has also increased its attacks on unpatched Exchange Servers since Microsoft announced the vulnerability.
It’s worth noting that the vulnerability does not apply to Office 365 Exchange Online, only to the on-premises versions of Microsoft’s email server platform. A CISA alert sent out on Saturday, March 6, 2021, warned that “Successful exploitation of these vulnerabilities allows an unauthenticated attacker to execute arbitrary code on vulnerable Exchange Servers, enabling the attacker to gain persistent system access, as well as access to files and mailboxes on the server and to credentials stored on that system.”
Despite Microsoft issuing patches almost eight months ago, 61% of Exchange servers are still vulnerable. The vulnerability in question, identified as CVE-2020-0688, exists in the control panel of Microsoft Exchange’s mail and calendaring server. The flaw, which stems from the server’s failure to create unique keys during installation, was fixed as part of Microsoft’s February 2021 Patch updates. Microsoft warned security administrators that unpatched servers were being exploited by unnamed threat actors earlier this month.
Minimizing Security Gaps With
CSP Authenticator+
Modern authentication methods represent a more robust security structure, and also provide a better user experience when logging into applications. MFA also makes it easier for auditors to get answers to critical compliance questions; providing information such as which users are granted access to which system, and also how the access policy is being reliably enforced. Additionally, some of the modern MFA applications available today also include reporting capabilities, which ensure that compliance standards, such as PCI DSS, are being met.
CSP Authenticator+™ supports numerous authentication factors for NonStop. It provides a RESTful interface that supports multi-factor authenticated logins on NonStop systems. CSP Authenticator+ resides on the NonStop Platform and uses an OSS “bridge” to connect to the RESTful interface of the CSP Authenticator+ web server.
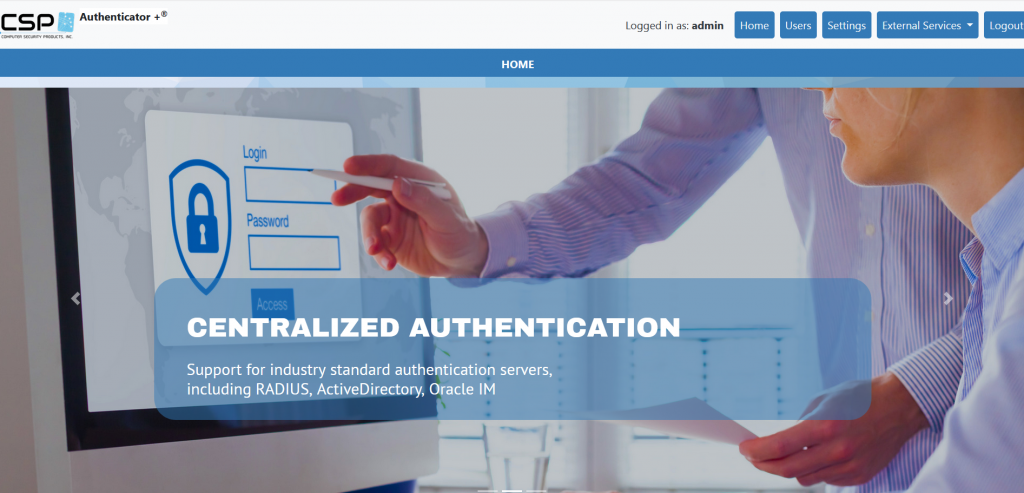
CSP Authenticator+™ Dashboard
CSP Authenticator+ can provide authentication services via Safeguard Authentication SEEP, or Pathway and Non-Pathway servers. Almost any application, including TACL, can now easily support multi-factor authentication (MFA).
Authentication methods such as RADIUS, RSA Cloud, Active Directory, and Open LDAP are supported. Additional authentication methods include RSA SecurID, Email, Text Message, and Google Authenticator. You can now enable MFA logins for different applications, making them more secure!
CSP Authenticator+ Key Features:
- Support for various authentication methods
- Browser-based user-friendly interface
- Standardized authentication across platforms
- Configurable for all or selected users
- Support for virtual addressing
CSP – Compliance at your Fingertips™
For complimentary access to CSP-Wiki®, an extensive repository of NonStop security knowledge and best practices, please visit wiki.cspsecurity.com
We Built the Wiki for NonStop Security ®
+1(905) 568 –8900












